Watch video on YouTube here: https://youtu.be/SE8ZuGKw4Eg by NetSec
|
In this video, I am gonna use Portainer to demonstrate how to install AList into your own Linux VPS and how to run AList from your Windows machine. I also shows how to configure your own domain and use NPM to do reverse proxy with SSL certificate to enable HTTPS access. AList can be used in a ouple of use cases, such as central cloud management portal, central media sharing portal, or even to replace your NAS. It worths taking your time to explore the usage of AList. Related Post: ✍https://blog.51sec.org/2022/12/5-minutes-docker-series-deploy-free.html Related Videos: ?Using Docker Run to Deploy AList - A File Index App for Local/Cloud Storages - https://youtu.be/9ZFgm-5w8HY 5 Minutes Docker Series: ? Install A Web Notepad App - Minimalist - https://youtu.be/8Ea1-6Knl-g ? Install An Open Source Personal Music Streaming Server - koel - https://youtu.be/9ZrGV0zFbSw ? Deploy Wordpress in CentOS 7 with Docker - https://youtu.be/9whAlZIfEKE ? Using Portainer Deploy Minimalist Online Notepad & Using NPM Enable HTTPS with Basic Authentication - https://youtu.be/vWyE6qn-46o ? Deploy A File Index App for Local / Cloud Storages - AList - https://youtu.be/9ZFgm-5w8HY ? Using Docker Run to Deploy AList - A File Index App for Local/Cloud Storages - https://youtu.be/9ZFgm-5w8HY ?Chapters: 0:00 - Introduction 2:37 - Lets start it! 3:31 - Use Portainer to Install AList 4:46 - 2. Config Own Domain and Reverse Proxy with HTTPS access 11:02 - 3. Deploy AList to Local Windows Machine 17:17 - End Scene ✅#51Sec #NetSec ====================================================================== If you found this video has some useful information, please give me a thumb up and subscribe this channel to get more updates: ⚡https://www.youtube.com/c/Netsec?sub_confirmation=1 ⚡Resource Collection and Bookmarks: https://sites.51sec.org/ Learning and Sharing - ?海内存知己,天涯若比邻 https://51sec.org https://itprosec.com
Watch video on YouTube here: https://youtu.be/SE8ZuGKw4Eg by NetSec
0 Comments
This video introduces AList, an open source project from Github, to list your files/folders from multiple storage places, either local or cloud. Although it is similar as other projects I introduced before, such as , GOIndex, GDIndex, OneManager, OnePoint, etc. This one is still under active maintenance and having more features. Related Post: ✍,https://blog.51sec.org/2022/12/5-minutes-docker-series-deploy-free.html Related Videos: ⚡Using Cloudflare Workers to Create a Serverless Google Drive Indexer with New Theme (GoIndex) - https://youtu.be/5O4zQc4pvDs ⚡Create a Serverless Fast OneDrive Index (FODI) Site Using Cloudflare Workers and GitHub Page - https://youtu.be/WE8qxkcJTlI ⚡Using Cloudflare Workers to Build Free Google Drive Indexer (GoIndex) in 5 Minutes - https://youtu.be/HjKjB8JKa08 ⚡Deploy GitHub Project OneManager using Heroku and Cloudflare to List OneDrive Content - https://youtu.be/aJ0SEUSeDZ4 ⚡Deploy OneManager (OneDrive Manager) to Heroku and Overcome Usage limitation Using Cloudflare Worker - https://youtu.be/RZZto9TGyxA 5 Minutes Docker Series: ? Install A Web Notepad App - Minimalist - https://youtu.be/8Ea1-6Knl-g ? Install An Open Source Personal Music Streaming Server - koel - https://youtu.be/9ZrGV0zFbSw ? Deploy Wordpress in CentOS 7 with Docker - https://youtu.be/9whAlZIfEKE ? Using Portainer Deploy Minimalist Online Notepad & Using NPM Enable HTTPS with Basic Authentication - https://youtu.be/vWyE6qn-46o ? Deploy A File Index App for Local / Cloud Storages - AList - https://youtu.be/9ZFgm-5w8HY ?Chapters: 0:00 - Introduction 2:24 - Lets start it 4:26 - 1. Deploy AList Using Docker Run 8:10 - 2. Mount Local Storage 10:27 - 3. Mount Google Drive Storage 15:10 - End Scene #51Sec #NetSec ====================================================================== If you found this video has some useful information✍, please give me a thumb up ✅ and subscribe this channel ?to get more updates?: ⚡https://www.youtube.com/c/Netsec?sub_confirmation=1 ⚡Resource Collection and Bookmarks: https://sites.51sec.org/ Learning and Sharing - ?海内存知己,天涯若比邻 ⚡https://51sec.org ?https://itprosec.com
Watch video on YouTube here: https://youtu.be/9ZFgm-5w8HY by NetSec [5 Minutes Docker Series] Deploy A Free File List App for Multiple Cloud Storages - Alist12/25/2022
[5 Minutes Docker Series] Deploy A Free File List App for Multiple Cloud Storages - Alist
AList is a file list program that supports multiple storage, powered by Gin (back end) and Solidjs (front end). It is similar as some other programs I used before in this blog. You can find related posts regarding them, such as OnePoint, GoIndex, OneManager, FODI (Fast OneDrive Index), :
So far, based on my experience and testing for all of those Cloud Drive File Listing program, AList is best, OnePoint is second. Others are still having some critical function / feature missing.
Related Sites for this AList project:
Introduction
This file list program, Alist, supports multiple storage, and supports web browsing and webdav, powered by gin and Solidjs
Features:
Docker Run to DeployUsagestable version
beta version (not recommended)
Initial password refer to logs.Use the following command after running the above command:
Noets:
Docker Hub site:
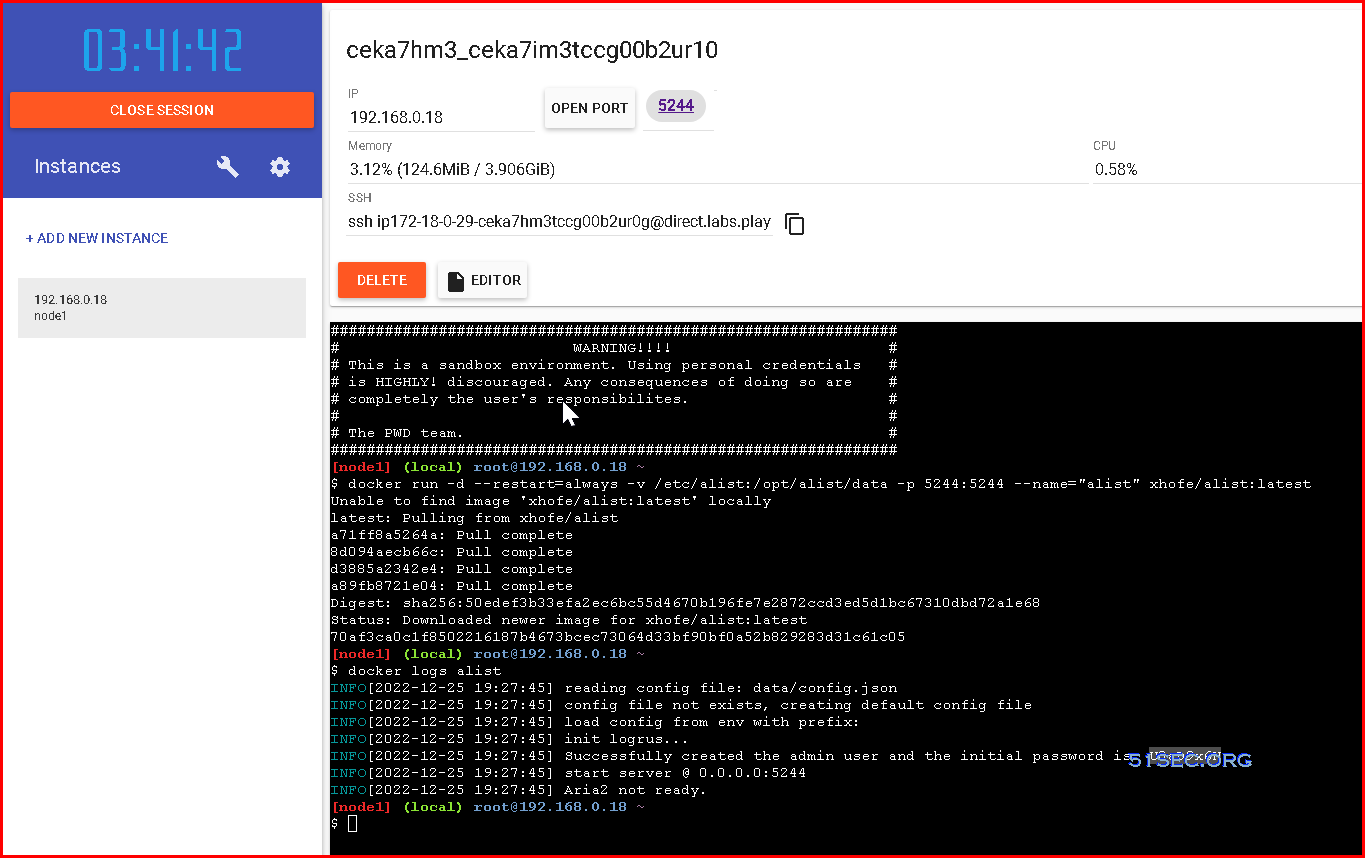
Docker Run AList from https://labs.play-with-docker.com/
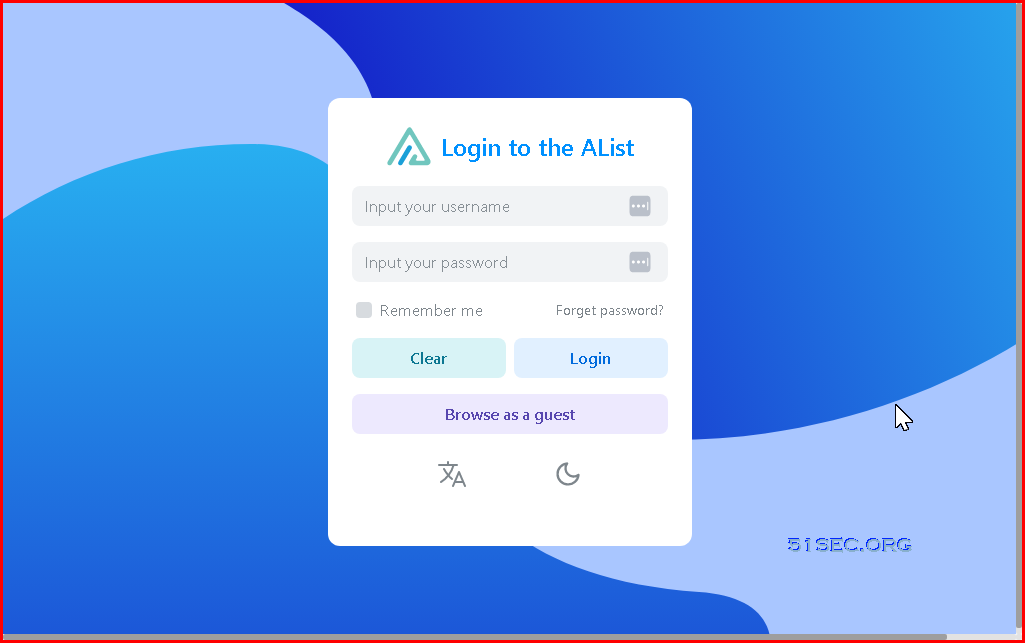
Login to Alist with the admin username and the found password from logs:
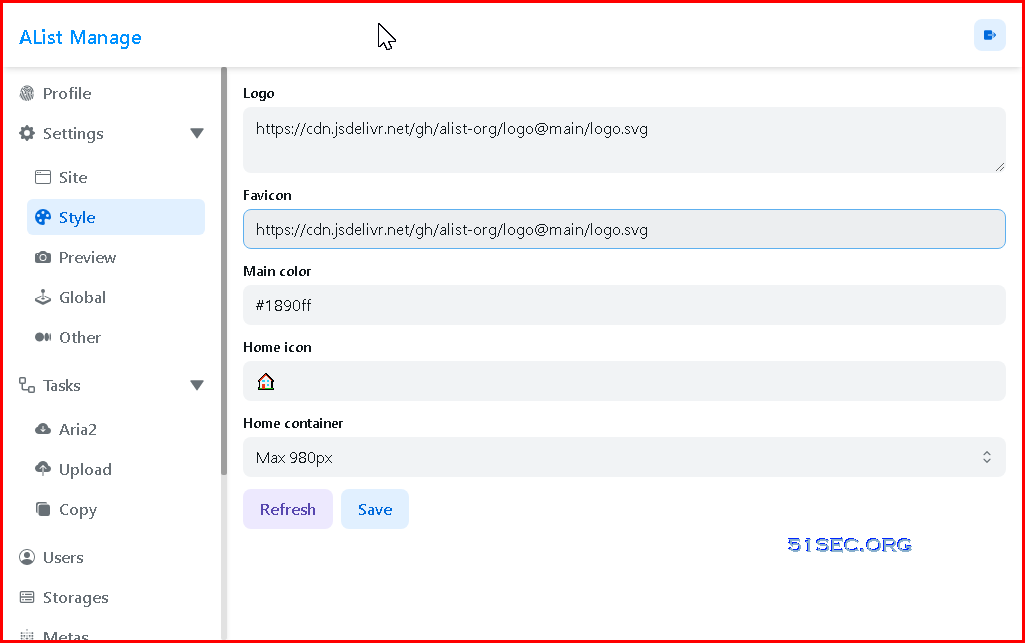
AList Manage backend:
You can change your AList App's logo, favicon, home icon and home container style:
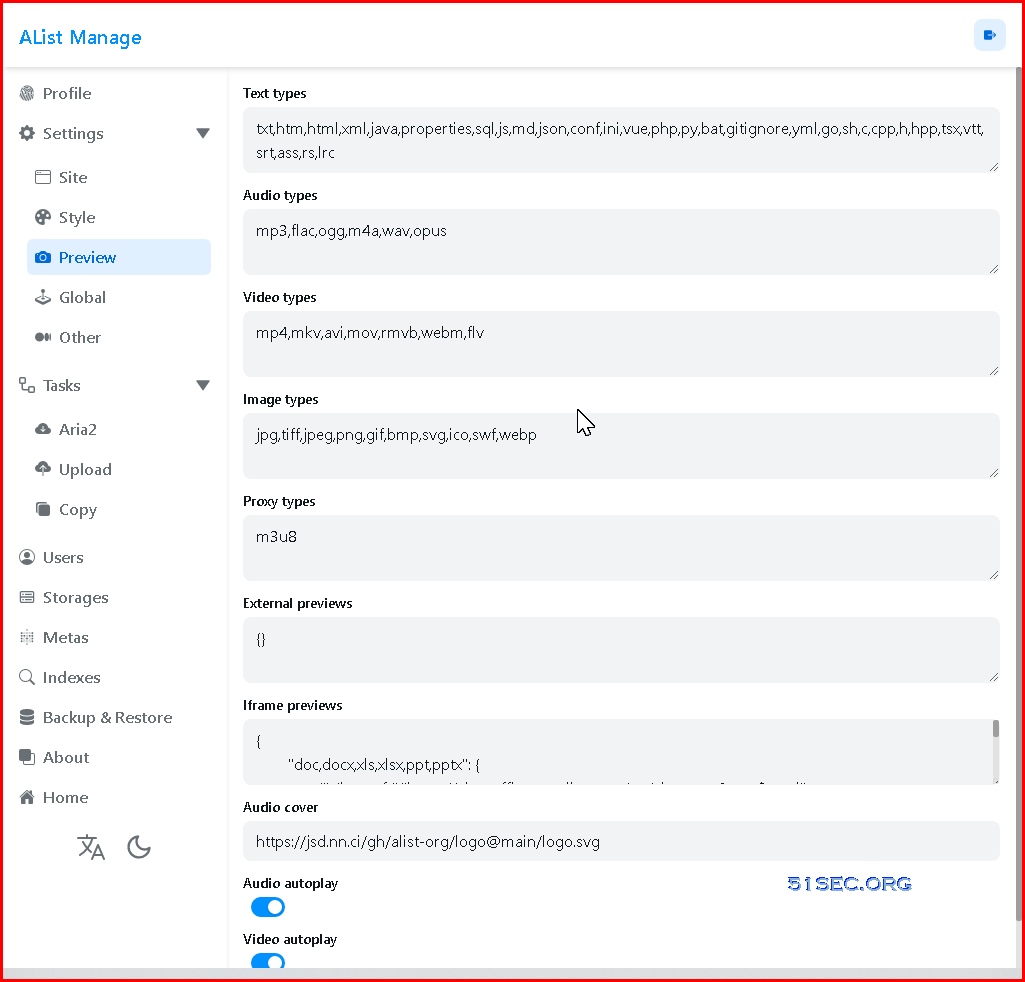
Supported Preview File Type:
PaaS To Deploy AlistThe initial password refer to logs. Koyeb​Render​Railway​Easy to use but easy to violate ToS too. Heroku​
Notes:
There are some issues for Heroku deployment. Here is one FAQ post mentions some issues: https://elements.heroku.com/buttons/cqchenqin/alist-heroku
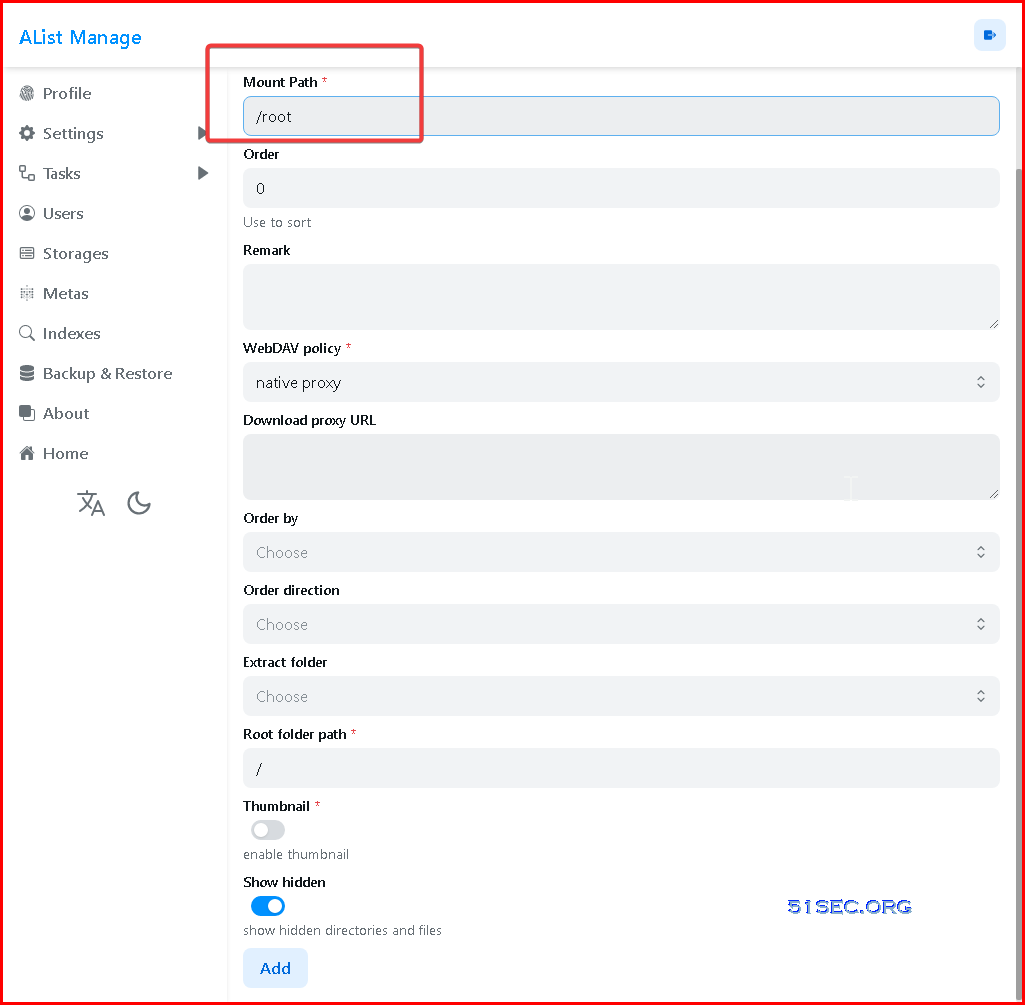
Free Database for PaaS DeploymentYou may need to use another remote MySQL database as instance restarts will lose data. Recommended Free MySQL Databases: Add StoragesLocalGoogle Drive:
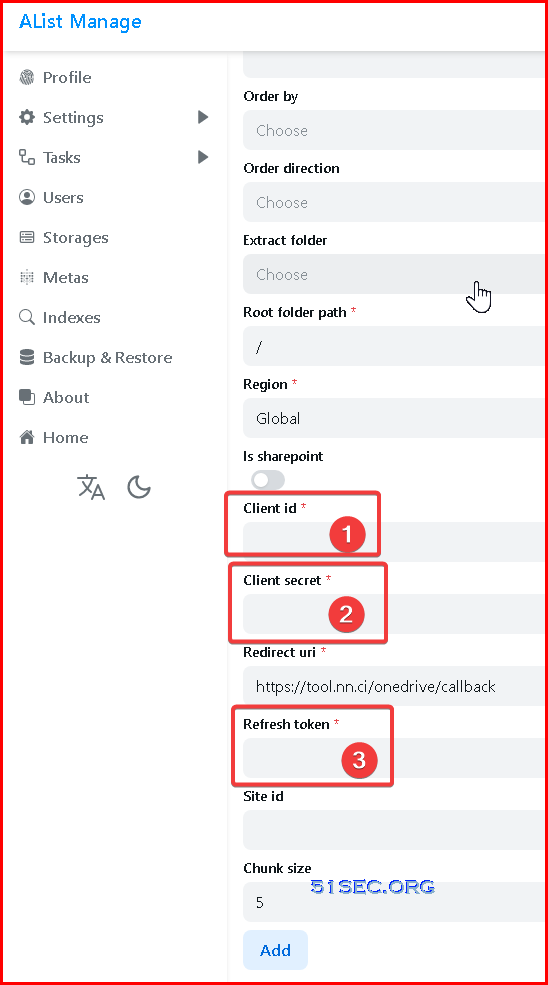
If you have your own Client ID, Client Secret, and refresh token, you can directly paste them in here. As to how to get your own Google Drive's following information, I will put them into another post to talk about it.
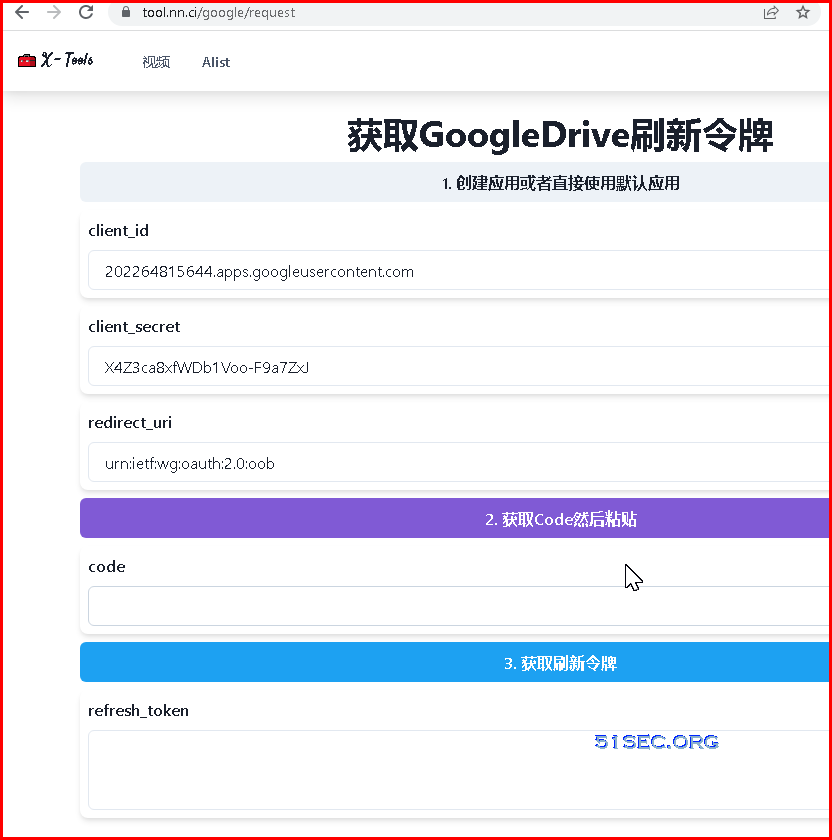
To make it simple, you can use a default client id / client secret to generate your refresh_token for your Google drive folder, using https://tool.nn.ci/google/request:
After you collected all those information, you can enter them into this AList page to add your Google Drive folder to show all the files / folders.
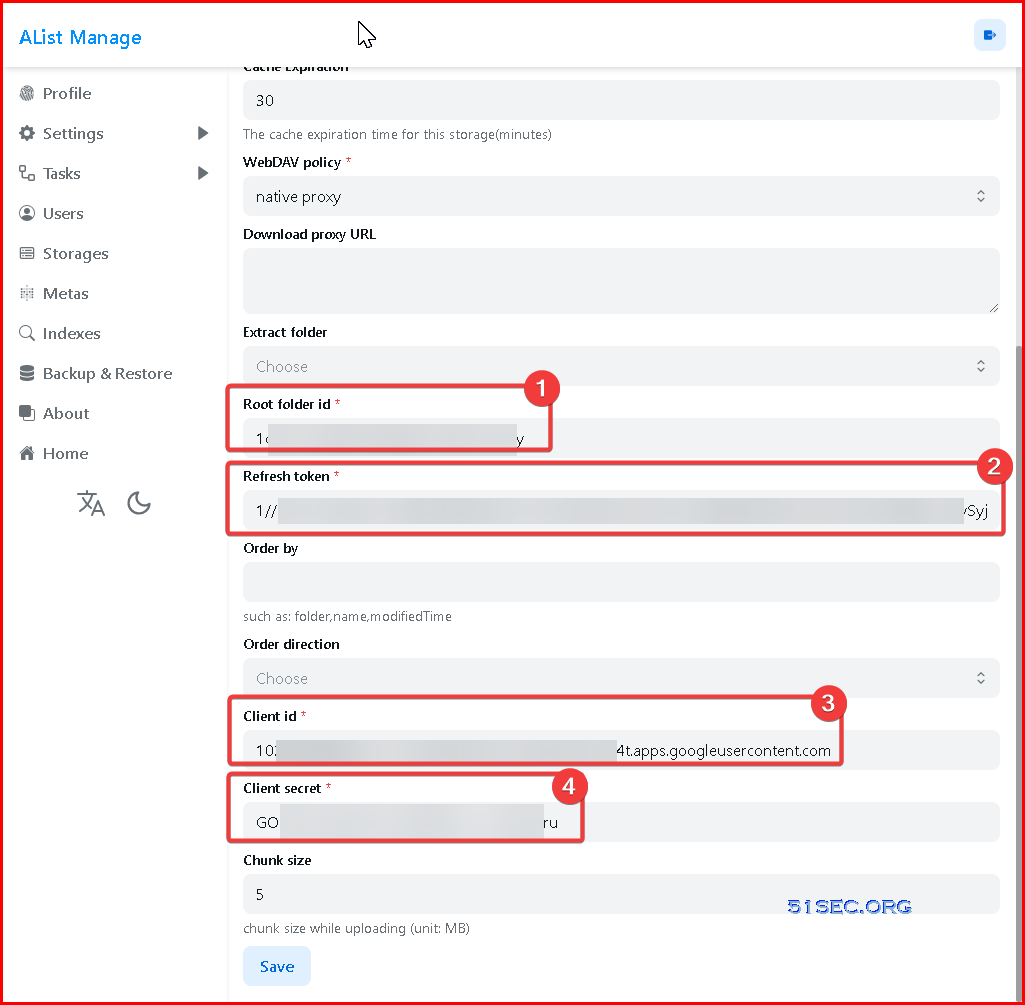
OneDrive:
Same as Google Drive, it had better to have your own client id
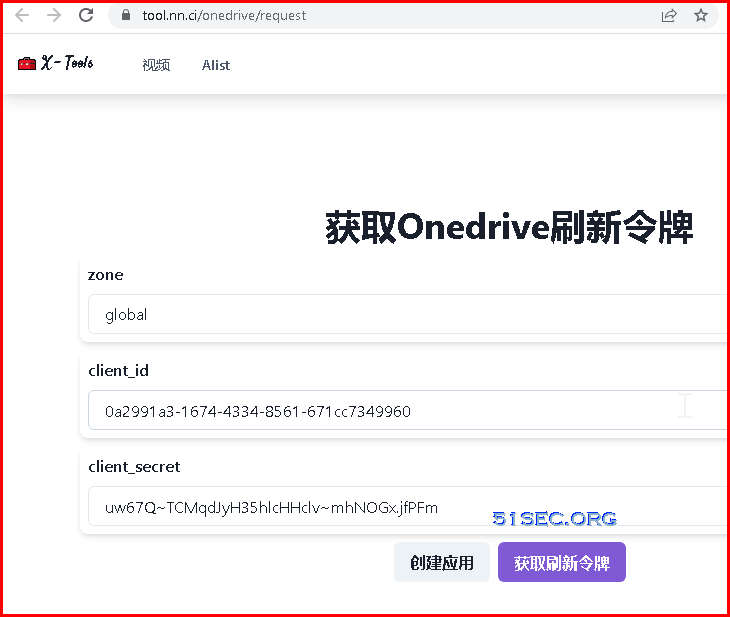
To make it simple, we also can use https://tool.nn.ci/onedrive/request to generate all information.
VideosOnline AList Sites
Some collected AList sites as demo:
via Blogger http://blog.51sec.org/2022/12/5-minutes-docker-series-deploy-free.html December 25, 2022 at 04:52PM Cloud
This video is to continue my Barracuda lab , starting configuring LAN and WAN interfaces, Firewall access rules and NAT rules. All are basic but it shoule be helpful to get you an idea how to start configuring this powerful Barracuda firewall. Related Post: ✍,https://blog.51sec.org/2022/12/barracuda-firewall-access-list-policy.html ✍https://blog.51sec.org/2022/11/barracuda-cloudgen-firewall-f12-initial.html Related Videos: ?Barracuda CloudGen Firewall F12 Initial Configuration - https://youtu.be/dP_0dO7LO8E ?Config Basic Barracuda CloudGen FW Firewall Access & NAT Rules - https://youtu.be/ZzVlsZxTtew 00:00 - Introduction 01:35 - Log into Firewall Dashboard 02:46 - Configure LAN/WAN Interfaces 08:28 - Config a Pass Rule for ICMP Traffic 11:56 - Create a DST NAT Rule for RDP Traffic 16:10 - End #51Sec #NetSec ====================================================================== If you found this video has some useful information✍, please give me a thumb up ✅ and subscribe this channel ?to get more updates?: ⚡https://www.youtube.com/c/Netsec?sub_confirmation=1 ⚡Resource Collection and Bookmarks: https://sites.51sec.org/ Learning and Sharing - ?海内存知己,天涯若比邻 ⚡https://51sec.org ?https://itprosec.com
Watch video on YouTube here: https://youtu.be/ZzVlsZxTtew by NetSec
Barracuda Firewall Access-list Policy Lab
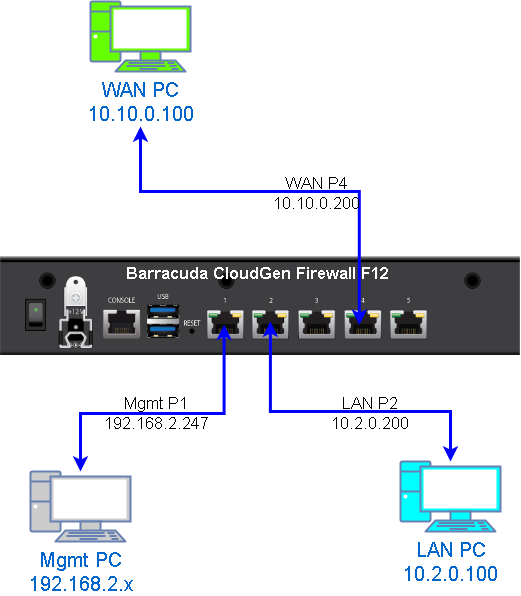
This post is going to show a basic initial configuration for Barracuda CloudGen Firewall F12. Topology
Online PNG Format Topology Diagram:
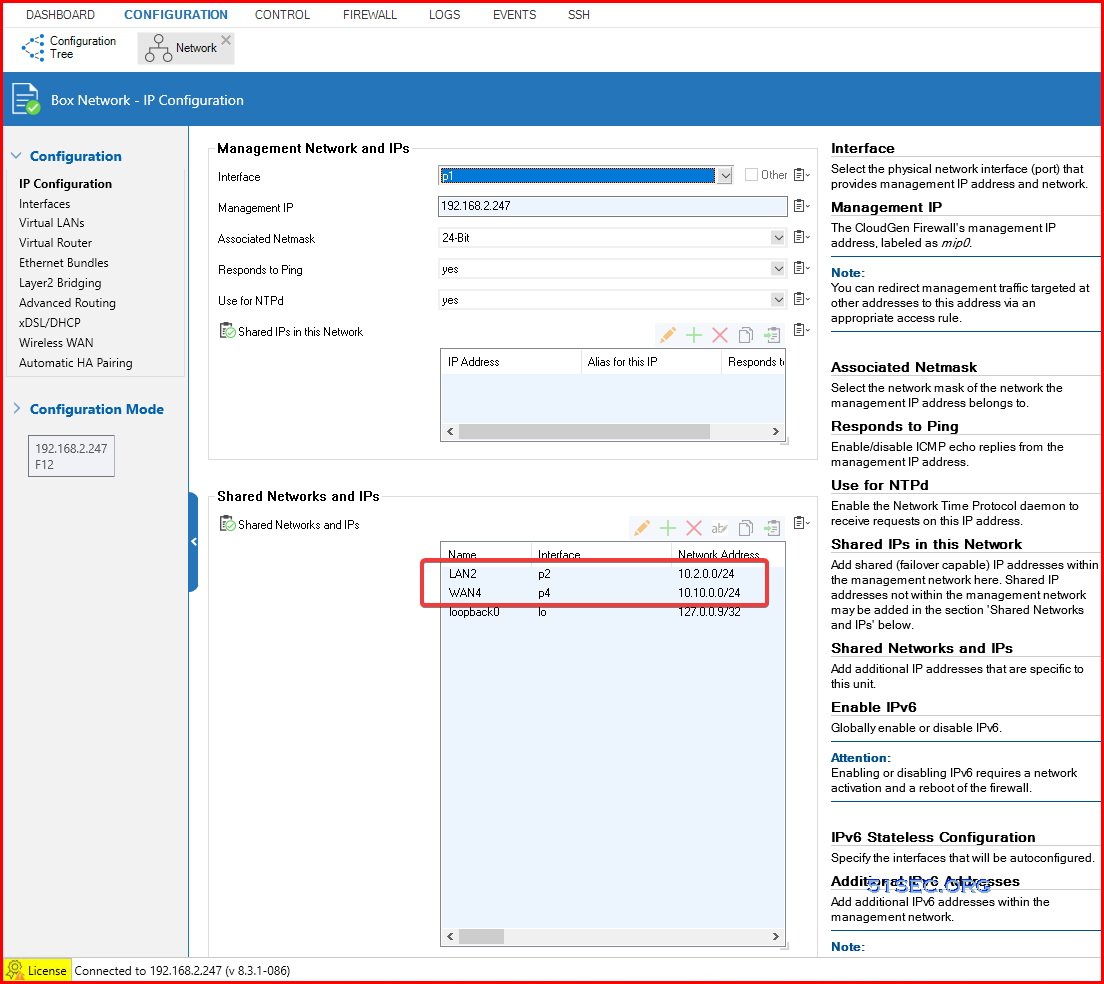
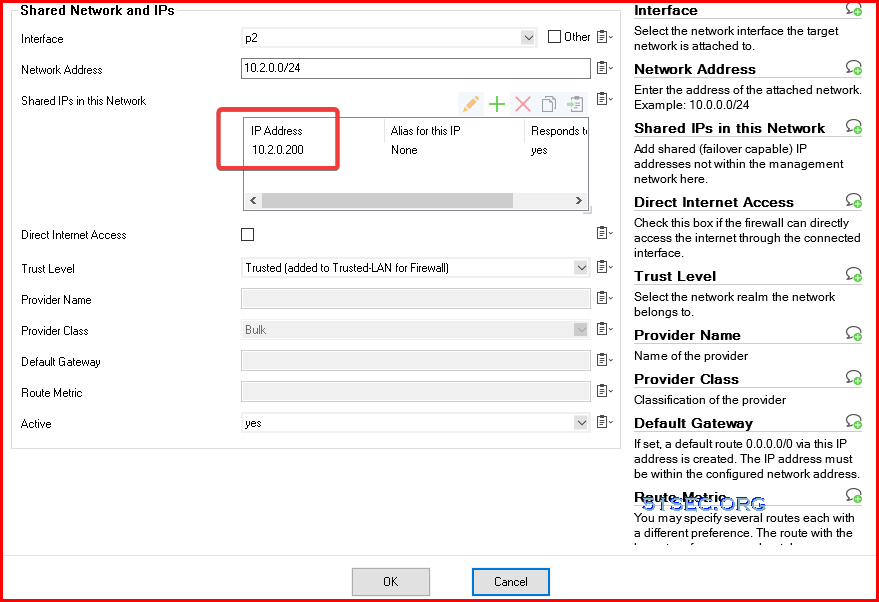
Configure InterfacesGo to Configuration - IP Configuration - Shared Networks and IPs:
Add LAN and WAN interfaces in with corresponding configuration:
Configure Forwarding Firewall Rule
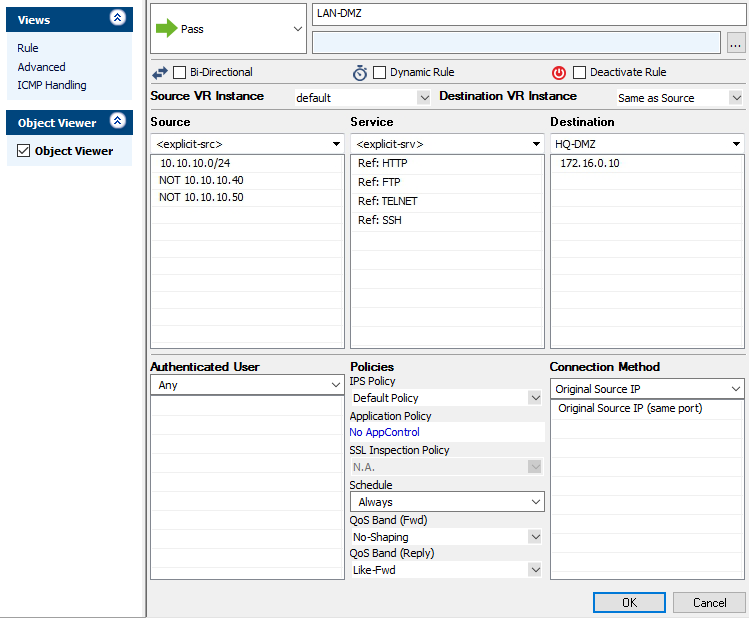
A Pass access rule permits traffic for a specific Service coming from the Source to access the selected Destination . For the Source and Destination , you can specify network objects, IP addresses, networks, or geolocation objects .
Note: https://campus.barracuda.com/product/cloudgenfirewall/doc/79462929/how-to-create-a-pass-access-rule/
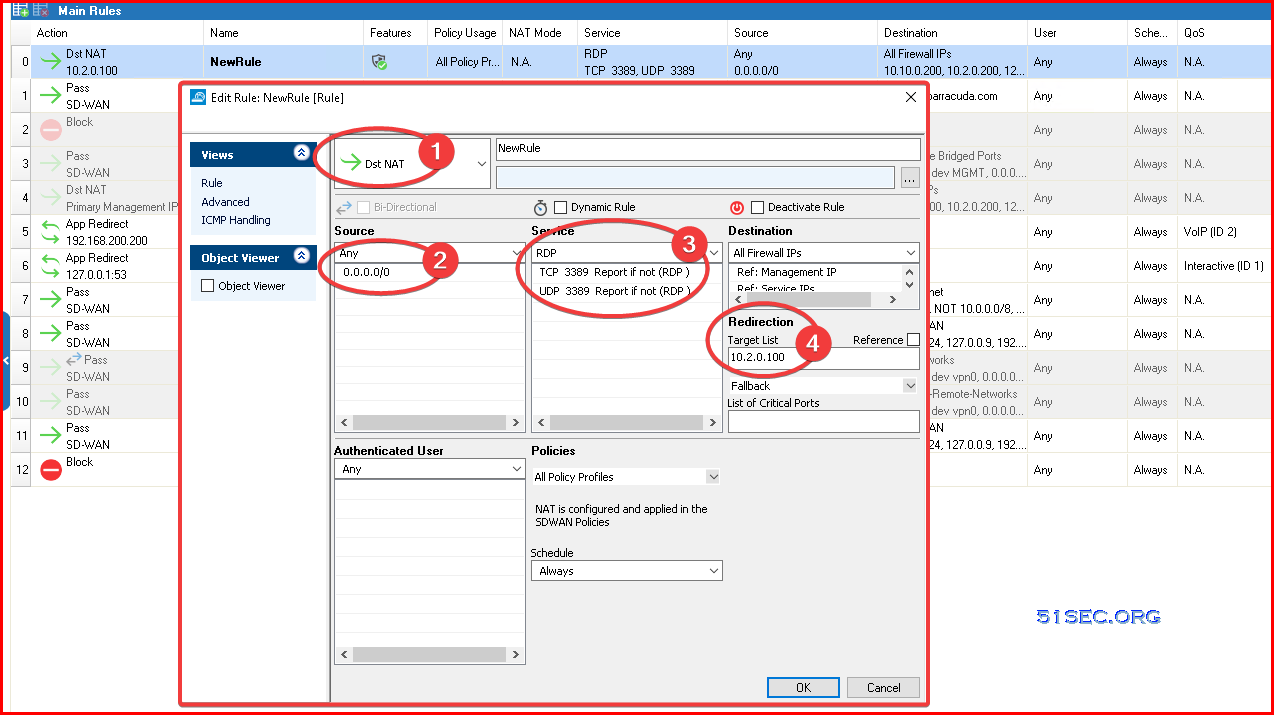
Configure Destination NAT Firewall RuleA Dst NAT access rule redirects traffic that is sent to an external IP address to a destination in the internal network. The following example shows a Dst NAT rule allowing HTTP and HTTPS access from the Internet to a server in the DMZ (172.16.0.10). The redirect target can be a single IP address or hostname, or a network object. Hostnames and IP addresses can be appended with a port number to redirect the traffic to a different port.via Blogger http://blog.51sec.org/2022/12/barracuda-firewall-access-list-policy.html December 24, 2022 at 11:45AM Security
Cybersecurity Governance Overview
Cybersecurity governance refers to the component of governance that addresses an organization's dependence on cyberspace in the presence of adversaries. The ISO/IEC 27001 standard defines cybersecurity governance as the following:
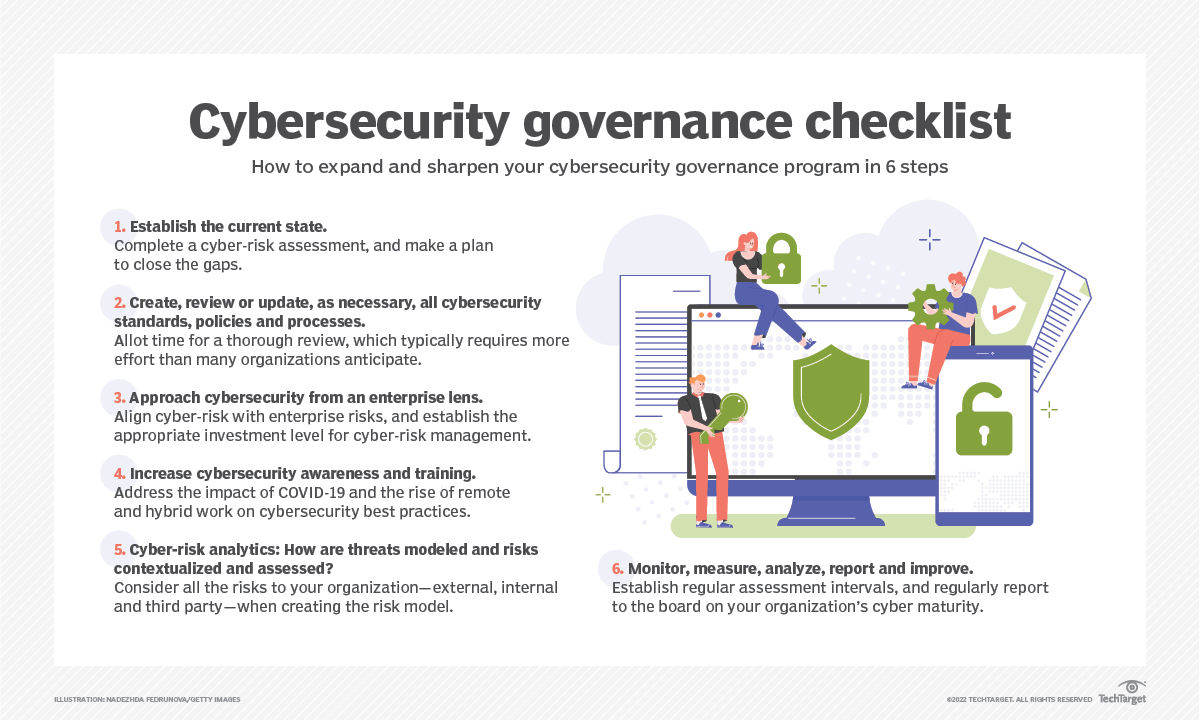
IntroductionTraditionally, cybersecurity is viewed through the lens of a technical or operational issue to be handled in the technology space. Cybersecurity planning needs to fully transition from a back-office operational function to its own area aligned with law, privacy and enterprise risk. The CISO should have a seat at the table alongside the CIO, COO, CFO and CEO. This helps the C-suite understand cybersecurity as an enterprise-wide risk management issue -- along with the legal implications of cyber-risks -- and not solely a technology issue. The C-suite can then set the appropriate tone for the organization, which is the cornerstone of any good governance program. Establishing the right tone at the top is much more than a compliance exercise. It ensures everyone is working according to plan, as a team, to deliver business activities and ensure the protection of assets within the context of a risk management program and security strategy. Historically, cybersecurity was managed by implementing a solution to solve a problem or mitigate a risk. Many cybersecurity departments have technical security safeguards, such as firewalls or intrusion detection, but often lack basic cybersecurity governance policies, best practices and processes. Where they do exist, policies or processes are often outdated or ignored. Many cybersecurity departments also have poor or inadequate cybersecurity awareness training programs that fail to address all levels of an organization. As we have learned from recent breaches, many organizations have inadequate hardening and patching programs. Poor access control practices, such as uncontrolled group passwords, shared accounts, proliferated admin privileges, shared root access and the absence of an authorization process except at a low operational level, also are problematic. Here are six steps that can help an organization grow and sharpen its cybersecurity governance program:
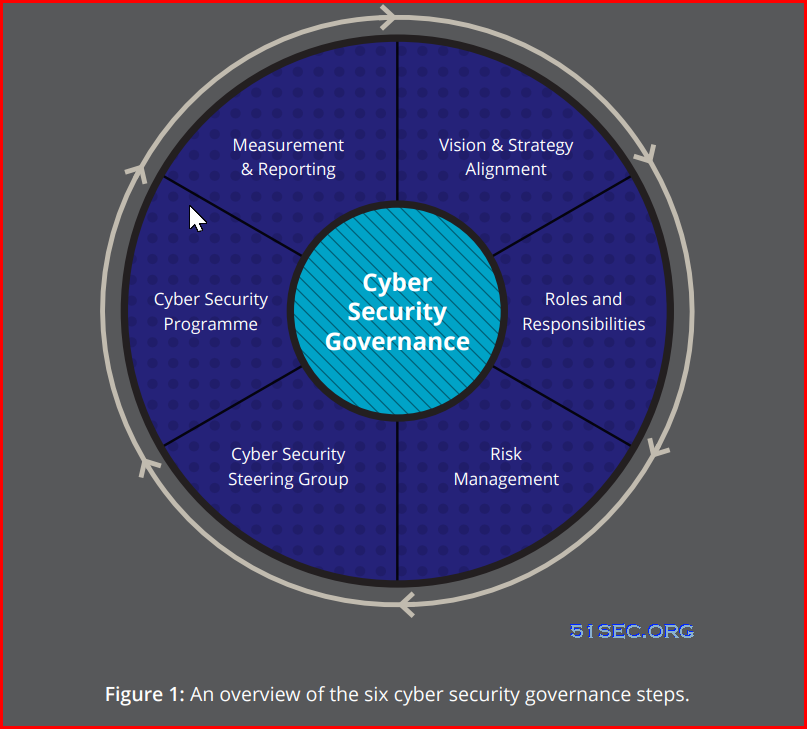
Another similar six cyber security governance steps diagram:
Note: https://www.ncsc.govt.nz/assets/NCSC-Documents/NCSC-Cyber-Security-Governance.pdf
Build Cyber Security Governance Step Example1. Create Cybersecurity Transformation
1.1 ESTABLISH CURRENT STATE
As a first step, the current state of cybersecurity and the existing governance model should be assessed and established. This means that, beyond the assumptions that may have existed before, cybersecurity in its present state should be described “as is,” including all weaknesses and deficiencies. Typically, this includes any systemic weaknesses previously identified (see previous section) and the pain points that have triggered the need for transformation. The underlying objective is to go from the initial observation that “we cannot go on like this” to a more constructive view of existing information security governance, management and assurance. The current state review will also reveal any weaknesses in management attitudes. As described previously, neither the minimalist nor the “zero tolerance” attitude are likely to lead to success. Part of establishing the current state of cybersecurity is to identify the exact position of the enterprise in terms of attitudes, beliefs and security spending behavior. In summary, the governance model selected by the enterprise is likely to provide a lot of insight on what may have led to the, apparently unsatisfactory, current state. Taking stock in this manner may be a painful exercise. However, it is indispensable as a starting point in transforming cybersecurity. Only where weaknesses have been recognized beyond doubt, and clearly articulated, will the enterprise be able to transition to an improved way of governing cybersecurity.
1.2 DEFINE TARGET STATE
Once the existing state of cybersecurity is known and fully acknowledged, the future or target state may be defined based on weaknesses and deficiencies, risk and vulnerabilities, and the extent to which the enterprise will be able to change and adapt to the trends in attacks, breaches and incidents. Where the target state is not clearly understood, it is unlikely that a transformation approach will be successful.
Typical pitfalls include:
• Lack of realism—The target state is formulated as a wish list for perfection, rather than the next obvious (and stable) state of overall cybersecurity.
• Escalating commitment—The target state is defined as “just a little more of what we are doing now,” without incorporating the changed threat and vulnerability landscape, not to mention actual attacks and breaches.
• Blurred vision—The target state is defined based on wrong assumptions—e.g., where organizational management does not incorporate future trends in cybercrime and cyberwarfare.
• Governance model bias—The current governance model (e.g., “zero tolerance” or “we are insured”) is maintained, ignoring strong signals that it may be dysfunctional.
In transformation thinking, the target from a governance perspective is to identify the next stable—and, therefore, achievable—level at which cybersecurity will be able to meet the needs of stakeholders, and at which there will be a reasonable level of protection against attacks and breaches. Transforming cybersecurity is a repetitive and iterative exercise that resembles a life cycle rather than a one‐off project.
1.3 STRATEGIC AND SYSTEMIC TRANSFORMATION
The distance between the current and future states of overall cybersecurity is subject to governance as well as management. Once the target state has been identified and defined, there are two dimensions of change that need to be planned, managed and monitored. The strategic dimension covers setting strategy, planning and implementing high‐level steps, and initiating a program and related portfolio of cybersecurity projects. The systemic dimension addresses dependencies between parts of the cybersecurity system that will have an impact on how change will be achieved and what will be the immediate and secondary effects.
Transforming cybersecurity in a systemic way also means that any changes will need to be examined with regard to unwelcome side effects. As an example, the deployment of an awareness program for employees may be beneficial in terms of improving vigilance and attention to detail. However, an unwelcome secondary result might be that a large number of “false positives” increases the cost of incident management and
distracts attention from real (but unobtrusive) APT attacks. More complex dependencies may exist in cybersecurity systems that will only come to light if the transformation is seen as a systemic and holistic exercise. 2. ESTABLISHING CYBERSECURITY GOVERNANCE
Information security governance in general sets the framework and boundaries for security management and related solutions. This necessarily includes formal policies, procedures and other elements of guidance that the agencies are required to follow. However, where governance in its best sense means “doing the right things,” it needs to take into account that a large part of cybersecurity is concerned with handling unexpected events and incidents.
Cybersecurity governance is both preventive and corrective. It covers the preparations and precautions taken against cybercrime, cyberwarfare and other relevant forms of attack. At the same time, cybersecurity governance determines the processes and procedures needed to deal with actual incidents caused by an attack or security breach. In this context, governance principles and provisions must be reasonably flexible to allow for the fact that attacks are often unconventional, generally against the rules, and most often designed to circumvent exactly those procedures and common understandings within the organization that keep the business running. Establish Cybersecurity governance with following six‐step approach as explained below: STEP 1: IDENTIFY STAKEHOLDER NEEDS
STEP 2: MANAGE CYBERSECURITY TRANSFORMATION STRATEGY.
STEP 3: DEFINE CYBERSECURITY STRUCTURE Structure
Roles and Responsibilities
Communications
Integration
STEP 4: MANAGE CYBERSECURITY RISKS
STEP 5: OPTIMIZE CYBERSECURITY RESOURCES
STEP 6: MONITOR CYBERSECURITY EFFECTIVENESS
Note: https://www.moheri.gov.om/userupload/Policy/Cyber%20Security%20Governance%20Guidelines.pdf
Cybersecurity: Governance vs ManagementCyber security governance should not be confused with cyber security management. Cyber security management is concerned with making decisions to mitigate risks; governance determines who is authorized to make decisions. Governance specifies the accountability framework and provides oversight to ensure that risks are adequately mitigated, while management ensures that controls are implemented to mitigate risks. Management recommends security strategies. Governance ensures that security strategies are aligned with business objectives and consistent with regulations.NIST describes IT governance as the process of establishing and maintaining a framework to provide assurance that information security strategies are aligned with and support business objectives, are consistent with applicable laws and regulations through adherence to policies and internal controls, and provide assignment of responsibility, all in an effort to manage risk. Governance: doing the right thing. Management: doing things right.
Cyber Security : Governance vs OperationMaking the organizational move from a divided hierarchy to one in which strategy informs operation (and operation informs strategy) is a difficult challenge. Communication is key to effectively managing expectations, messaging, and security posture throughout the process. Detect, prioritize, and controlOperational controls – the real-life response to a cybersecurity incident – should be the focus of any security program. Managing these controls and reporting to a governance structure may not require the knowledge of operationalization, but instead may rely on an agreed-upon level of confidence in respect to risk management involving both governance and operational leadership. In addition to working alongside governance experts, operational controls managers should measure their security posture against a framework or baseline such as the CIS Controls™ or NIST Cyber Security Framework. Conducting such an assessment is important, as understanding your organization’s compliance levels is key to finding weaknesses in the organizational controls as well as the prioritization of investment for strengthening controls. A previous blog post discussed calculating your risk-reduction ROI; after identifying weaker controls, we can start to use this single calculation to define what provides the greatest level of return on investment as well as the greatest reduction in risk. In future blog posts, risk will be discussed with respect to quantitative analysis, using a Monte Carlo simulation to demonstrate how a single risk and control mitigation can provide an overall reduction in risk to the whole organization. With clearer reporting and analysis of risk reduction, we can bridge the gap between governance and operational security, leading to better strategic decision making and a more unified approach to the cyber threat landscape.
Note: https://www.cisecurity.org/insights/blog/breaking-the-divide-between-governance-and-operational-cybersecurity
Plan - Do - Check - Act modelThe ICGM utilizes a Plan, Do, Check & Act (PCDA) approach that is a logical way to design a governance structure:
Note: https://www.linkedin.com/pulse/integrated-cybersecurity-governance-model-plan-do-check-tom-cornelius/
 Plan – Policies & StandardsDo – Controls & ProceduresCheck – Reporting & AssessmentsAct – Risk Managementvia Blogger http://blog.51sec.org/2022/12/cybersecurity-governance-overview.html December 23, 2022 at 09:45AM Architecture
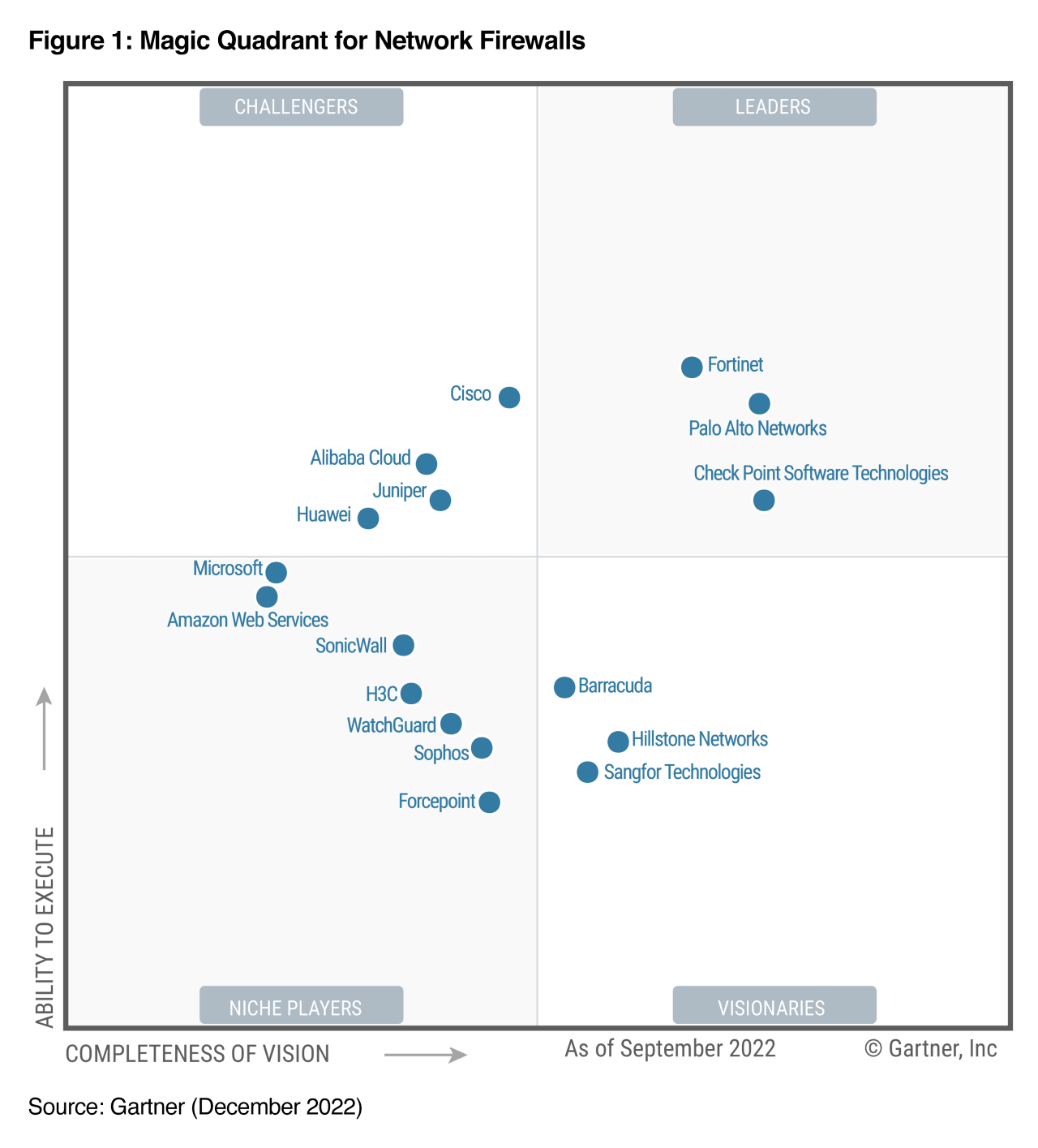
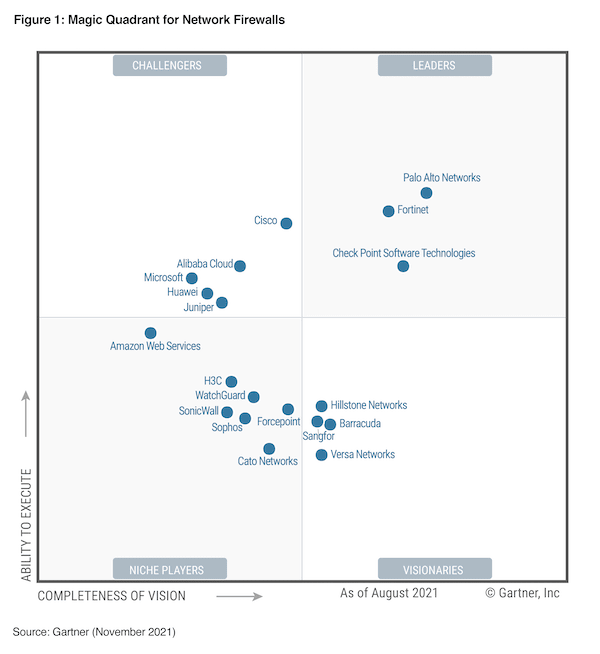
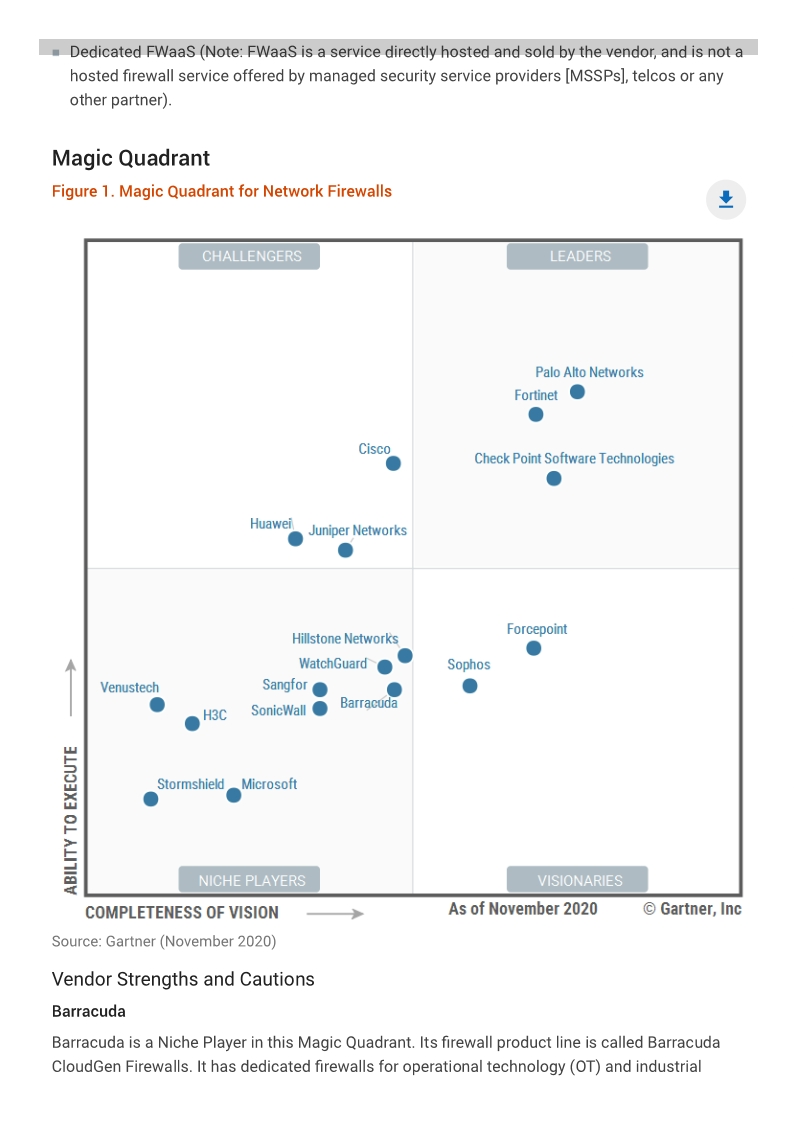
Gartner Magic Quadrant for Enterprise Network Firewall (2010-2022)
Based on Gartner's definition, the enterprise network firewall " is composed primarily of purpose-built appliances for securing enterprise corporate networks. Products must be able to support single-enterprise firewall deployments and large and/or complex deployments, including branch offices, multitiered demilitarized zones (DMZs) and, increasingly, the option to include virtual versions for the data center. Customers should also have the option to deploy versions within Amazon Web Services (AWS) and Microsoft Azure public cloud environments. These products are accompanied by highly scalable (and granular) management and reporting consoles, and there is a range of offerings to support the network edge, the data center, branch offices and deployments within virtualized servers and the public cloud. " Here is the difference from UTM appliance, which UTM approaches are suitable for small or midsize businesses (SMBs), but not for the remainder of the enterprise market. 20222021
Fortinet is in Leader quadrant since 2016.
20202019
2018 Gartner Magic Quadrant for Enterprise Network FirewallsCisco comes back to Leaders quadrant again. Palo Alto, Fortinet and Check Point are still doing well as Leaders.2017 Gartner Magic Quadrant for Enterprise Network Firewalls
2016 Gartner Magic Quadrant for Enterprise Network FirewallsReference: https://www.amerinet.com/sites/default/files/2016%20FW%20gartner%20report.pdf 2015 Gartner Magic Quadrant for Enterprise Network FirewallsGartner, Inc. has released the latest Magic Quadrant for Enterprise Network Firewalls on April 22, 2015: The biggest change in this year is Juniper lost their challengers position in the magic quadrant based on following reasons. In 2010 Juniper was in leaders quadrant:
"Juniper is assessed as a Niche Player for enterprises, mostly because we see it selected in concert with other Juniper offerings, rather than displacing competitors based on its vision or features, and we see it being replaced in enterprise environments more often than we see it selected. Juniper is, however, shortlisted and/or selected in mobile service provider deployments and large-enterprise data center deployments, primarily because of price and high throughput on its largest appliances." - From Gartner report.
Other small changes from 2014 to 2015:
2014 Gartner Magic Quadrant for Enterprise Network Firewall:Palo Alto and Checkpoint position into leader quadrant again. This is the third year for Palo Alto and seventeenth year for Checkpoint to list in the leader quadrant. 2013 Gartner Magic Quadrant for Enterprise Network Firewall:
Note: There is no 2012 Gartner Magic Quadrant for Enterprise Network Firewall
2011 Gartner Magic Quadrant for Enterprise Network FirewallsGartner Magic Quadrant for Enterprise Network Firewall:2010 Gartner Magic Quadrant for Enterprise Network Firewall:Reference:via Blogger http://blog.51sec.org/2014/04/2014-gartner-magic-quadrant-for.html December 22, 2022 at 04:31PM Security Using Portainer Deploy Minimalist Online Notepad & Using NPM Enable HTTPS with Basic Authentication12/20/2022
My previous video has shown two ways to deploy this open source online notepad project - Minimalist. This video shows more advanced usages, such as enable https on your own custom domain, and enable basic authentication to protect your Web App. Related Post: ✍https://blog.51sec.org/2022/12/5-mins-docker-series-minimalist-web.html 5 Minutes Docker Series: ? Install A Web Notepad App - Minimalist - https://youtu.be/8Ea1-6Knl-g ? Install An Open Source Personal Music Streaming Server - koel - https://youtu.be/9ZrGV0zFbSw ? Deploy Wordpress in CentOS 7 with Docker - https://youtu.be/9whAlZIfEKE Related Videos: ?Get Two Free and Permanent VPS from Oracle Cloud Platform - https://youtu.be/E9dHA3NBbN8 ?Using Portainer to install NPM and Configure Domain Name Access for Management Portal of Portainer & NPM - https://youtu.be/_gKl_wtY_Gg ?Using Rclone To Add Cloud Drive(s) Into Your VPS and Execute Read/Write Performance Test - https://youtu.be/A_o9E1yx-O4 #51Sec #NetSec ====================================================================== If you found this video has some useful information✍, please give me a thumb up ✅ and subscribe this channel ?to get more updates?: ⚡https://www.youtube.com/c/Netsec?sub_confirmation=1 ⚡Resource Collection and Bookmarks: https://sites.51sec.org/ Learning and Sharing - ?海内存知己,天涯若比邻 ⚡https://51sec.org ?https://itprosec.com
Watch video on YouTube here: https://youtu.be/vWyE6qn-46o by NetSec
This video is to show you two different ways to install a Github project - Minimalist as your Web Notepad. It is a simple web appliction to get a notepad in your web browser and you can use it to collaborate with others over Internet. Related Post: ✍https://blog.51sec.org/2022/12/5-mins-docker-series-minimalist-web.html 5 Minutes Docker Series: ? Install A Web Notepad App - Minimalist - https://youtu.be/8Ea1-6Knl-g ? Install An Open Source Personal Music Streaming Server - koel - https://youtu.be/9ZrGV0zFbSw ? Deploy Wordpress in CentOS 7 with Docker - https://youtu.be/9whAlZIfEKE Related Videos: ?Get Two Free and Permanent VPS from Oracle Cloud Platform - https://youtu.be/E9dHA3NBbN8 ?Using Portainer to install NPM and Configure Domain Access for Management Portal of Portainer & NPM - https://youtu.be/_gKl_wtY_Gg ?Using Rclone To Add Cloud Drive(s) Into Your VPS and Execute Read/Write Performance Test - https://youtu.be/A_o9E1yx-O4 #51sec #NetSec ====================================================================== If you found this video has some useful information✍, please give me a thumb up ✅ and subscribe this channel ?to get more updates?: ⚡https://www.youtube.com/c/Netsec?sub_confirmation=1 ⚡Resource Collection and Bookmarks: https://sites.51sec.org/ Learning and Sharing - ?海内存知己,天涯若比邻 ⚡https://51sec.org ?https://itprosec.com
Watch video on YouTube here: https://youtu.be/8Ea1-6Knl-g by NetSec
Configure NTFS Permissions (Windows ACLs) on Azure File Share Folders
We can configure Windows access control lists (ACLs), also known as NTFS permissions, at the root, directory, or file level on directory and file level over mounted file share(s). While share-level permissions act as a high-level gatekeeper that determines whether a user can access the share, Windows ACLs operate at a more granular level to control what operations the user can do at the directory or file level. Both share-level and file/directory-level permissions are enforced when a user attempts to access a file/directory, so if there's a difference between either of them, only the most restrictive one will be applied. For example, if a user has read/write access at the file level, but only read at a share level, then they can only read that file. The same would be true if it was reversed: if a user had read/write access at the share-level, but only read at the file-level, they can still only read the file. There are multiple ways we can apply NTFS permission during your data migration by using other tools such as azcopy or robocopy. Here are some related posts:
In this post, I am going
Azure Share-Level Permission Mapping to NTFS Permission
Share-level permission = RBAC permissions:
The following table contains the Azure RBAC permissions related to this configuration. If you're using Azure Storage Explorer, you'll also need the Reader and Data Access role in order to read/access the file share.
Supported Windows ACLS (NTFS)
Azure Files supports the full set of basic and advanced Windows ACLs.
The following permissions are included on the root directory of a file share:
Mount the file share using storage account keyBefore you configure Windows ACLs, you must first mount the file share by using your storage account key. To do this, log into a domain-joined device, open a Windows command prompt, and run the following command. Remember to replace It's important that you use the
net use Z: \\<YourStorageAccountName>.file.core.windows.net\<FileShareName> /user:localhost\<YourStorageAccountName> <YourStorageAccountKey>
net use Z: \\<YourStorageAccountName>.file.core.windows.net\<FileShareName> /user:localhost\<YourStorageAccountName> <YourStorageAccountKey>
Example::
net use R: \\fileshare4test.file.core.windows.net\fstest /user:localhost\fileshare4test h1GUuy3YasaG1LLNjQLQ8wD9PpYtyeVY1MY6s4s11BJLJQTzyUaX69LzYsDVyYOKm3cXgrsvYOpX+AStkQD+zW==
Other Command:
Robocopy Command with permission to copy
Robocopy "F:\testshare" "R:\test" /COPY:DAT /SEC /MIR /R:10 /W:5 /V /ETA
azcopy Command with permission to copy
./azcopy.exe copy "F:\testshare\" "https://fileshare4test.file.core.windows.net/fstest/testfolder/?sv=2021-06-08&ss=bfqt&srt=sco&sp=rwdlacupiytfx&se=2022-09-13T05:11:14Z&st=2022-09-12T21:11:14Z&spr=https&sig=85MdmVM%2FGwPmAQSay0sDC1mCboxZZP62UdFnYmW1HHR%3D" --preserve-smb-info=true --preserve-smb-permissions=true --disable-auto-decoding=false --recursive --log-level=INFO
Videosvia Blogger http://blog.51sec.org/2022/12/configure-ntfs-permissions-windows-acls.html December 17, 2022 at 06:34PM Cloud |
|











 RSS Feed
RSS Feed
